The DNSSEC acronym stands for Domain Name System Security Extensions. It is a set of DNS protocol extensions that were introduced by the IETF) with the goal of signing DNS data to secure the domain name resolving process.
Why is DNS Sec Important?
It prevents third-parties from being able to forge records and guarantees a domain's identity by preventing:
DNS Cache Poisoning
A form of man-in-the-middle attack where attackers flood a DNS resolver with false DNS information. Sometimes these attacks can get a match by the law of large numbers and plant a false result into the cache of the DNS resolver. The DNS resolver then provides this erroneous or malicious web address to anyone seeking that website until the time-to-live (TTL) expires.
False zones
DNSSEC also protects against malicious DNS attacks that exploit the DNS system and provide phony results for zones that don't even exist, essentially exploiting gaps between zones. DNSSEC secures the entire zone and provides mechanisms to prevent gap exploitation in unsigned zones. This is also known as the authenticated denial of existence.
Can I enable DNSSec?
Login to plesk, click on DNSSEC icon. Click 'Sign the DNS zone' you will then see a page like this where you can configure the service. For most users the settings below should be optimal, when you have made your selection click OK and the zone will be signed.
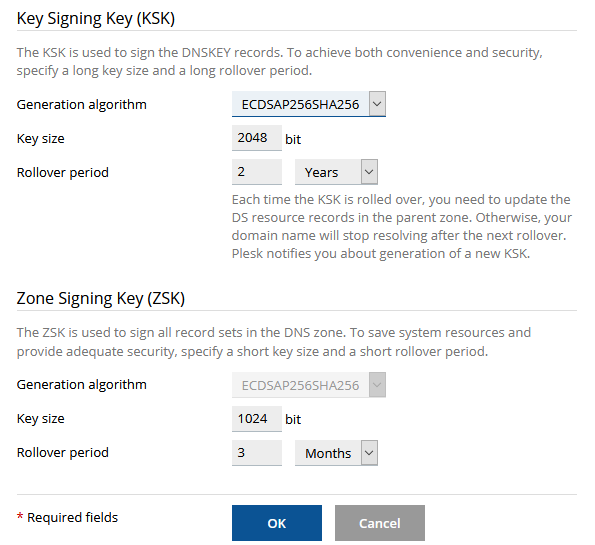
When the Zone is signed you will be given a series of DS records which must be attached to your domain name at the registry. See the article Here on how to add these records to your domain name which completes the trust chain and finalizes the process.
How Key Rollover Works
In order to prevent DNS outage for a domain, we use more than one key as the KSK (Key Signing Keys) and more than one key as the ZSK (Zone Signing Key). A previously generated key exists in parallel with a new key for some time, to allow all the changes in a DNS zone to take effect. Obsolete keys are removed automatically.
Use a long key and a long rollover period for the KSK (Key Signing Key).
Every time the Key Signing Key is updated, the zone owner needs to update the DS records in the parent domain zone. The recommended policy helps to update DS records in the parent zone as seldom as possible without decreasing security.
Note: It's important that the email address saved in the hosting control panel be kept up to date, i.e. use a generic role based email address rather than your personal one otherwise the system may not be able to notify you of the key expiry if the staff member has gone.


